Terraform allows infrastructure to be expressed as code in a simple, human readable language called HCL (HashiCorp Configuration Language) It reads configuration files and provides an execution plan of changes, which can be reviewed for safety and then applied and provisionedTerraformprovideraws aws_iam_role_policy_attachment 리소스가에 대한 새 값을 생성했지만 현재는 없습니다 에 만든 년 01월 31일 5 코멘트 출처 hashicorp/terraformprovideraws Similarly, in the worker role, we are permitting EC2 instances to assume roles and then attaching the managed policies AmazonEKSWorkerNodePolicy, AmazonEC2ContainerRegistryReadOnly, and AmazonSSMManagedInstanceCore to the worker role To execute the IAM script run below commands terraform plan terraform apply auto

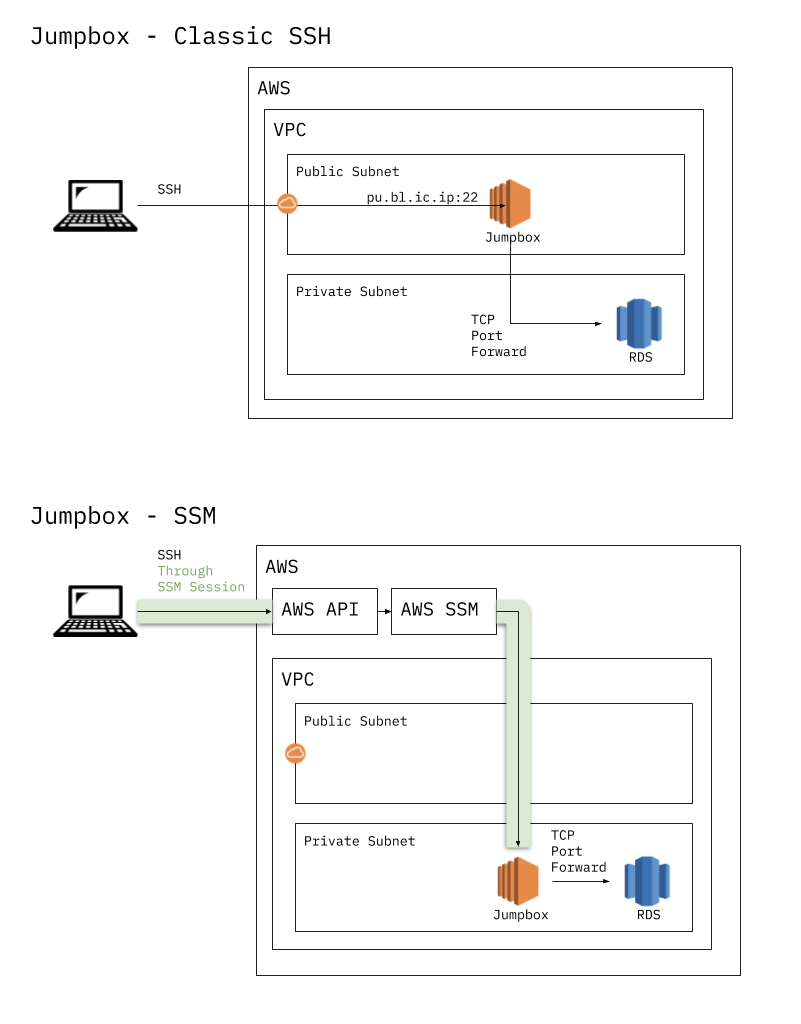
Login From Internet Into A Private Subnet With Session Manager By Giuseppe Borgese Medium
Amazonssmmanagedinstancecore terraform
Amazonssmmanagedinstancecore terraform-Additionally it will create one security group and one IAM role with the AmazonSSMManagedInstanceCore policy attached to the IAM role for the instance Have a look into maintf Note that this module is written for terraform client ver 014 or later Use release earlier releases for prior terraform versions VariablesIam Role string The IAM Role to attach to the managed instance Description string The description of the resource that you want to register Expiration Date string UTC timestamp in RFC3339 format by which this activation request should expire The default value is




Stop Exposing Port 22 To The World It S Time To Rework Your Remote Access Methods Toolr Io
Terraform Module POC for AWS Network Firewall I created this module in Terraform so you can do the test as well and also you can start from there and customize it for your environment I publish the code on the terraform registry on this page To run in your environment you can do it like that and in few minutes you can have a working POC How To Add An EC2 Instance To AWS System Manager (SSM) Hello Everyone Welcome to CloudAffaire and this is Debjeet In the last blog post, we have discussed how to install AWS System Manager (SSM)The default value is 24 hours from resource creation time Terraform will only perform drift detection of its value when present in a configuration iam_role (Required) The IAM Role to attach to the managed instance registration_limit (Optional) The maximum number of managed instances you want to register The default value is 1 instance
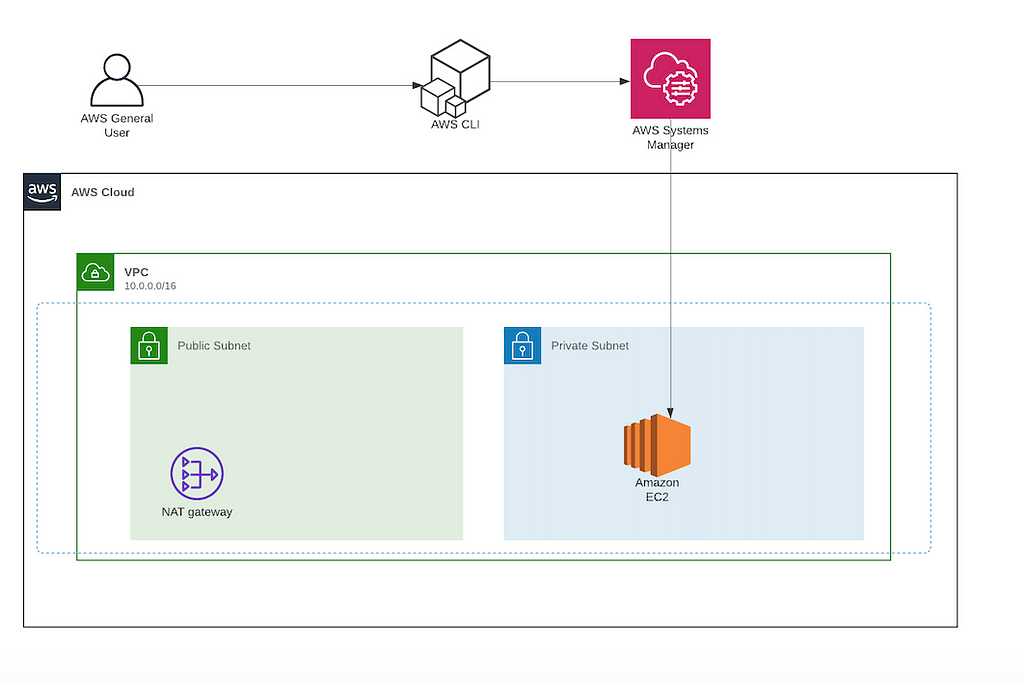
After the Part 1 post, which specifically explaining configuration with packer, on this part, I'll write more about Terraform and AWS Codebuild The final state that we'd like to have is something like this 2 Terraform I will build the whole stack using Terraform Before we start, we need a code repository to store our code Nginx CloudWatch Agent GitHub Gist instantly share code, notes, and snippets Using SSM Session Manager, we can now connect to our private instances directly without Bastion Hosts You don't need to open any ports, not even ssh port in your security groups to IPs or CIDR blocks This adds additional layer of security to your EC2 instances
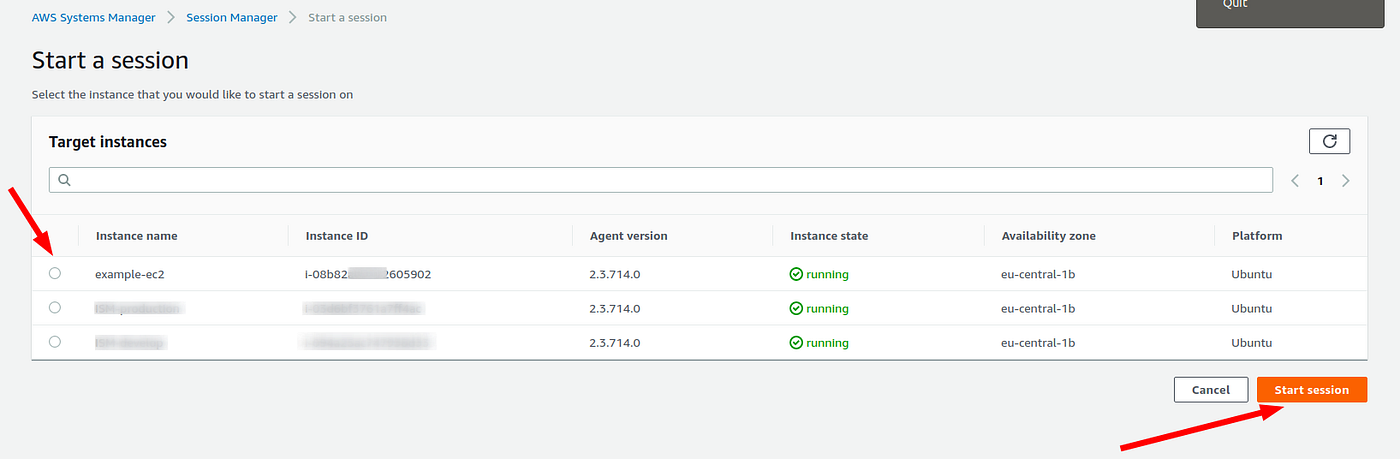
Resource aws_iam_role_policy_attachment The usage of this resource conflicts with the aws_iam_policy_attachment resource and will permanently show a difference if both are defined For a given role, this resource is incompatible with using the aws_iam_role resource managed_policy_arns argumentMETHOD 1 To connect Linux EC2 Instances , Select the instance and then click Start Session It will open a browser bases shell in the new tab You will be logged in as ssmuserTo login as root user , Enter sudo su If you go back to Systems manager console , You can find all the sessions created for an EC2 instance by an IAM user I have a aws_directory_service_directory resource defined in a service, which creates a security group that allows ports to be accessible from 0000/0 and this is getting flagged by security hub because AWS CIS standards do not recommend allowing ingress from 0000/0 for TCP port 33 My question is on how to restrict some of the rules in the




Secure Rds Access Through Ssh Tunneling Over Aws Ssm In Terraform




Applying Managed Instance Policy Best Practices Aws Management Governance Blog
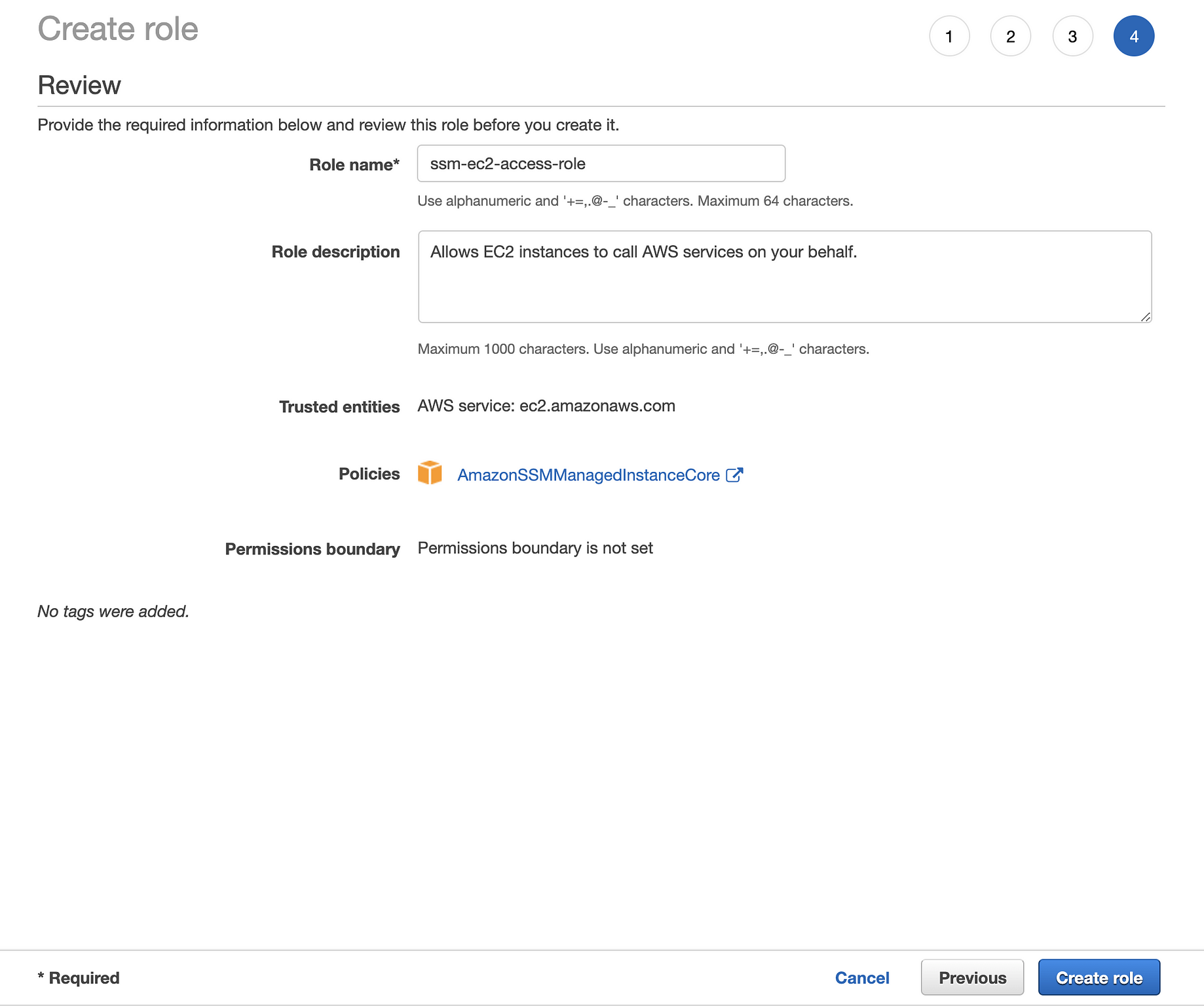
Sin embargo, a diferencia de la mayoría de los argumentos, el valor de FOR_ACT debe conocerse antes de que Terraform realice cualquier acción de recursos remotos Esto significa que para_each no puede referirse a ningún atributo de recursos que no se conocen hasta después de que se aplique una configuración (como una identificación única Using for_each in a situation like this involves making a distinction between the labels you give to these objects within your Terraform configuration and the labels/ids that the remote system assigns to them, because the remote system's identifiers can change over time and are typically not known until after apply, but Terraform needs these keys to stay consistentThe first policy, AmazonSSMManagedInstanceCore, allows an instance to use AWS Systems Manager service core functionality Depending on your operations plan, you might need permissions represented in one or more of the other three policies




Setting Up A Bottlerocket Managed Node Group On Amazon Eks With Terraform Containers




Install Agent On Aws Ec2 Instances Using Terraform And Aws Systems Manager Lacework
The terraform code creates an azure key vault secret successfully during the first apply, but with consecutive applies, it still is trying to update the secret because of the changes in the expiration azuredevops terraform terraformproviderazure terraform012Terraform has been successfully initialized!CloudFormation, Terraform, and AWS CLI Templates Configuration to create an IAM role for EC2 instances to access to AWS Systems Manager (SSM) services, with the least permissions required




Install Agent On Aws Ec2 Instances Using Terraform And Aws Systems Manager Lacework




Gruntwork Newsletter November Laptrinhx
Terraform is distributed as a single binary Install Terraform by unzipping it and moving it to a directory included in your system's PATH You can find the SH56 checksums for Terraform 108 online and you can verify the checksums signature file which has been signed using HashiCorp's GPG key AWS EC2 RDP without exposing instance to public I'm planning to use AWS EC2 instances for the development purpose of my web application So, I will like to disable all the outbound ports except RDP (33) port The RDP port will only be open to a particular AWS Service (host) Users can access the host only after logging into AWS Console Run Command enables you to automate common administrative tasks and perform ad hoc configuration changes at scale You can use Run Command from the AWS console, the AWS Command Line Interface, AWS Tools for Windows PowerShell, or the AWS SDKs Run Command is offered at no additional cost Administrators use Run Command to perform the following




Iac Mit Aws Cdk




Setting Up A Bottlerocket Managed Node Group On Amazon Eks With Terraform Containers
Automated configuration of Session Manager without an internet gateway Session Manager is a fully managed AWS Systems Manager capability that you can use to manage your Amazon Elastic Compute Cloud (Amazon EC2) instances, onpremises instances, and virtual machines (VMs) through an interactive oneclick browserbased shell or through the AWS CLIThe Terraform Associate certification is for Cloud Engineers specializing in operations, IT, or development who know the basic concepts and skills associated with open source HashiCorp Terraform Candidates will be best prepared for this exam if they have professional experience using Terraform in production, but performing the exam objectives How I set up secure AWS RDS access using SSM and EC2 instance profile with terraform How I set up secure AWS RDS access using SSM and EC2 instance profile with terraform policy/AmazonSSMManagedInstanceCore;




Terraformでec2を使ったweb環境をつくろう Qiita




Terraform Multi Cloud Demo Part 3 Aws Infrastructure Dave S Blog
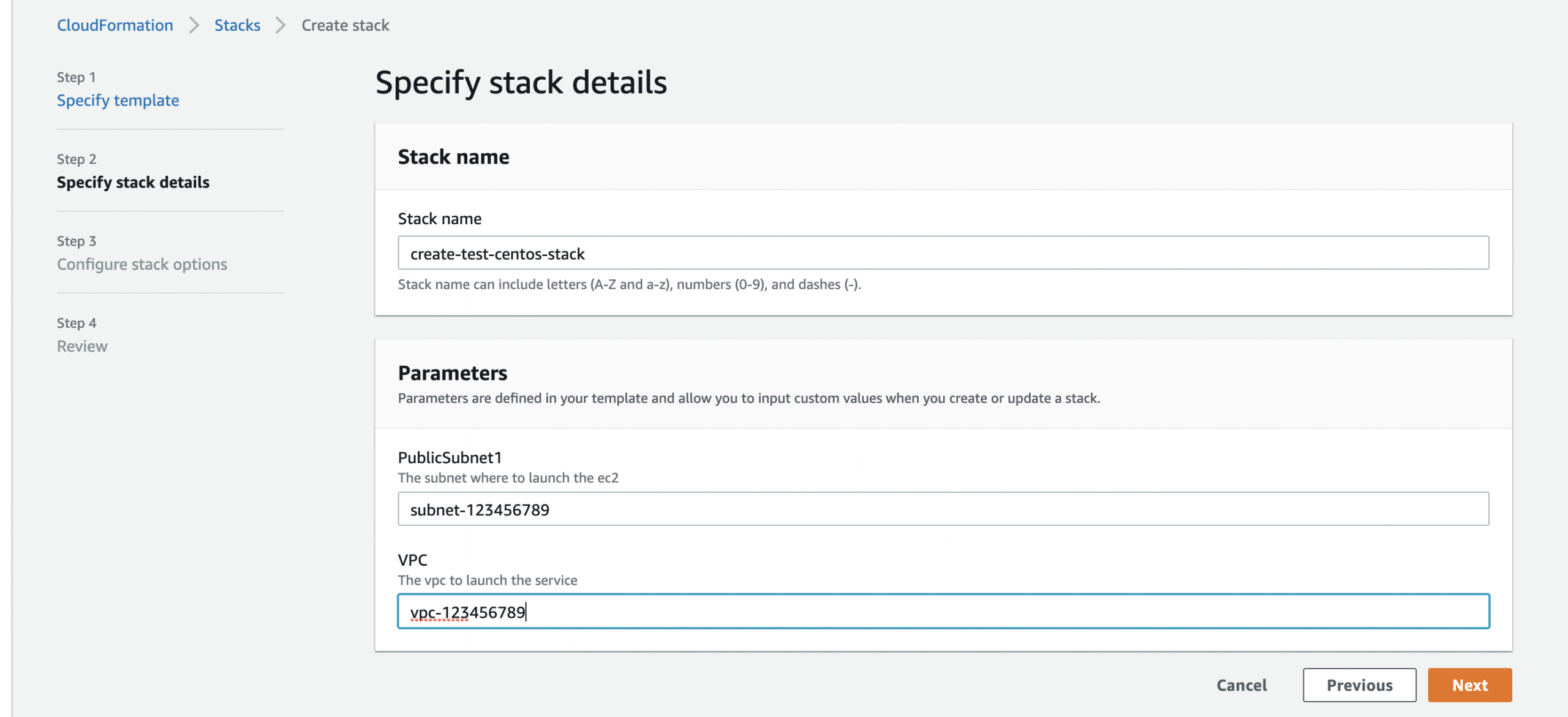
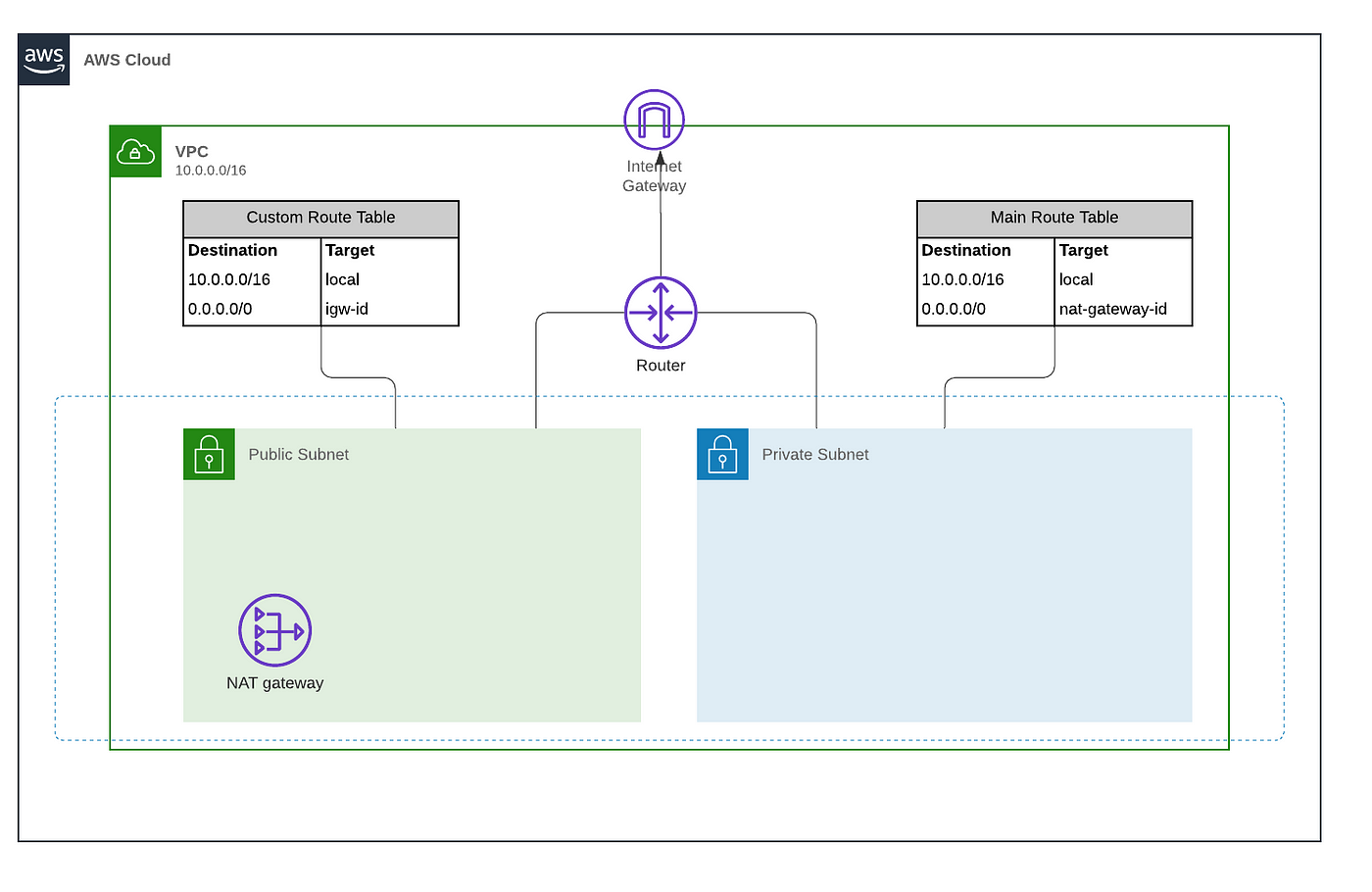
Create your VPC Creating a VPC with Terraform can be done by simply adding the following code block to your maintf file resource "aws_vpc" "tutorialvpc" { cidr_block = "/16" enable_dns_hostnames = true } The cidr_block parameter assigns 65,536 IP addresses to our VPC, and the enable_dns_hostnames enables the VPC to use DNS hostnamesThis doe The AWS Managed Policy AmazonSSMManagedInstanceCore offers a good starting IAM policy for the core actions required It can be used as a template policy for scoping down to specific resource sets In this tutorial I will show how to write Ec2 using terraform and access it through AWS SSM Here I am using the Ubuntu OSDynamic IAM Resources with Terraform IAM requirements differ between project to project Depending on the complexity, we could create the IAM resources with Terraform in the relevant layer However, having the IAM resources dynamically create within its own module, or even combining them with their resource counterparts, gives us great power



Terraform Aws Ec2 And Ssm Aws System Manager By Khimananda Oli Medium



Going Bastion Less Accessing Private Ec2 Instance With Session Manager Laptrinhx
After the outputs of running terraform init and terraform plan out plan look good, run a terraform apply to create the resources Once completed, we're ready to ssh onto the instance! $ terraform apply Plan 32 to add, 0 to change, 0 to destroy If you get any Terraform errors after applying, you might want to double check your code for any syntax errors or variable misreferences To access your blog, you will need to retrieve the DNS name of your application load balancer, in EC2 > Load Balancers > DescriptionThis Product Guide provides a detailed look at how Rackspace delivers our Fanatical Support for AWS offering It covers core concepts such as the AWS account structure, Rackspace service levels and advanced concepts such as providing access requests to instances via Rackspace Passport and accessing audit logs via Rackspace Logbook




Substitute Your Ssh Bastions Using Aws Systems Manager




Terraform Never Puts The Playbook Objects In S3 Githubmemory
You may now begin working with Terraform Try running "terraform plan" to see any changes that are required for your infrastructure All Terraform commands should now work If you ever set or change modules or backend configuration for Terraform, rerun this command to reinitialize your working directoryInstall EC2 instance connect on the bastion or update my AMI I found that EC2 instance connect comes preinstalled with certain terraform apply still does the refresh, that's why this issue is more frequent the more time elapses after applying Solution to it is just simply run terraform refresh before terraform destroy (even if your first destroy fails the one after refresh should go through)




Go X Next Js Spa をterraformでさっさと構築 3 3 たけログ




Automated Configuration Of Session Manager Without An Internet Gateway Aws Feed
The AWSSSMAssociation resource creates a State Manager association for your managed instances A State Manager association defines the state that you want to maintain on your instances For example, an association can specify that antivirus software must be installed and running on your instances, or that certain ports must be closedAdditionally it will create one security group and one IAM role with the AmazonSSMManagedInstanceCore policy attached to the IAM role for the instance Have a look into maintf Note that this module is written for terraform client ver 014 or later Use release earlier releases for prior terraform versions VariablesAlso, because of a bug in the Terraform registry (hashicorp/terraform#), the registry shows many of our inputs as required when in fact they are optional The table below correctly indicates which inputs are required Note add ${varssh_key_pair} private key to the ssh agent Include this repository as a module in your existing terraform




Install Agent On Aws Ec2 Instances Using Terraform And Aws Systems Manager Lacework




Instrumenting Amis For Gpu Monitoring On Cloudwatch Dev Community
Terraform automatically loads a number of variable definitions files if named the following way Files named exactly terraformtfvars or terraformtfvarsjson Any files with names ending in autotfvars or autotfvarsjson Now, create a new file to define the custom variables called terraformtfvars then add the following content Terraformprovideraws recurso aws_iam_role_policy_attachment produzido um novo valor para estava presente, mas agora ausente awspolicy/AmazonSSMManagedInstanceCore Usar a partição correta corrigiu o problema e não resultou neste erro A correção pode ser simplesmente uma mensagem de erro mais específicaEstablishing SSH Tunnel To begin, run the command ssh L 5432`terraform output raw rds_endpoint` Nf ubuntu@`terraform output raw bastion_ip`




Setting Up A Bottlerocket Managed Node Group On Amazon Eks With Terraform Containers




Login From Internet Into A Private Subnet With Session Manager By Giuseppe Borgese Medium
Running pulumi up and we have output about our EC2 after a few seconds Next, using SSM to connect (check here to set up the CLI), we just run aws ssm startsession target and we are in!What is exciting here is the whole script feels like familiar Typescript As much as I like working with Terraform or CloudFormation, those unfamiliar are sometimesThis Product Guide provides a detailed look at how Rackspace delivers our Fanatical Support for AWS offering It covers core concepts such as the AWS account structure, Rackspace service levels and advanced concepts such as providing access requests to instances via Rackspace Passport and accessing audit logs via Rackspace Logbook You can use AWS Systems Manager to automatically join a running instance to the domain You can host the domain on AWS Directory Service using AWS Directory Service for Microsoft Active Directory or Simple AD The domain can also be located over an onpremises network using the AD Connector directory gateway




Chaos Engineering Mit Dem Aws Fault Injection Service Fis




Setting Up A Bottlerocket Managed Node Group On Amazon Eks With Terraform Containers
Learning Terraform but wanted to ask you guys if CDK is looking to take over or not I personally find CDK harder to setup because some constructs requires setting up a VPC which isn't easy for an AWS newcomer Terraform is straightforward so far at least, but I



1



記事




Utilizando O Session Manager Aws System Manager Dev Community




Terraform Aws Ec2 With Ssm Agent Installed



How To Install Aws Ssm Agent On Centos 8 Centos 7 Computingforgeeks




Stop Exposing Port 22 To The World It S Time To Rework Your Remote Access Methods Toolr Io




Did You Know There Is A Better Way To Connect To Your Aws Linux Instances Than Ssh By Teracloud Sep 21 Medium




Cli Githubmemory




Did You Know There Is A Better Way To Connect To Your Aws Linux Instances Than Ssh




Secure Rds Access Through Ssh Tunneling Over Aws Ssm In Terraform




Did You Know There Is A Better Way To Connect To Your Aws Linux Instances Than Ssh




Terraformで Systems Manager Session Manager でアクセスできるようにしたec2インスタンスを構築する Qiita



90 Football Instant Score Net



Error Failed To Query Available Provider Packages With Hashicorp Iam After Adding Any Iam Data Issue Hashicorp Terraform Github




Using Aws Systems Manager Run Command To Submit Spark Hadoop Jobs On Amazon Emr Aws Management Governance Blog



Aws Terraform Ec2 Autorecovery Main Tf At Master Rackspace Infrastructure Automation Aws Terraform Ec2 Autorecovery Github
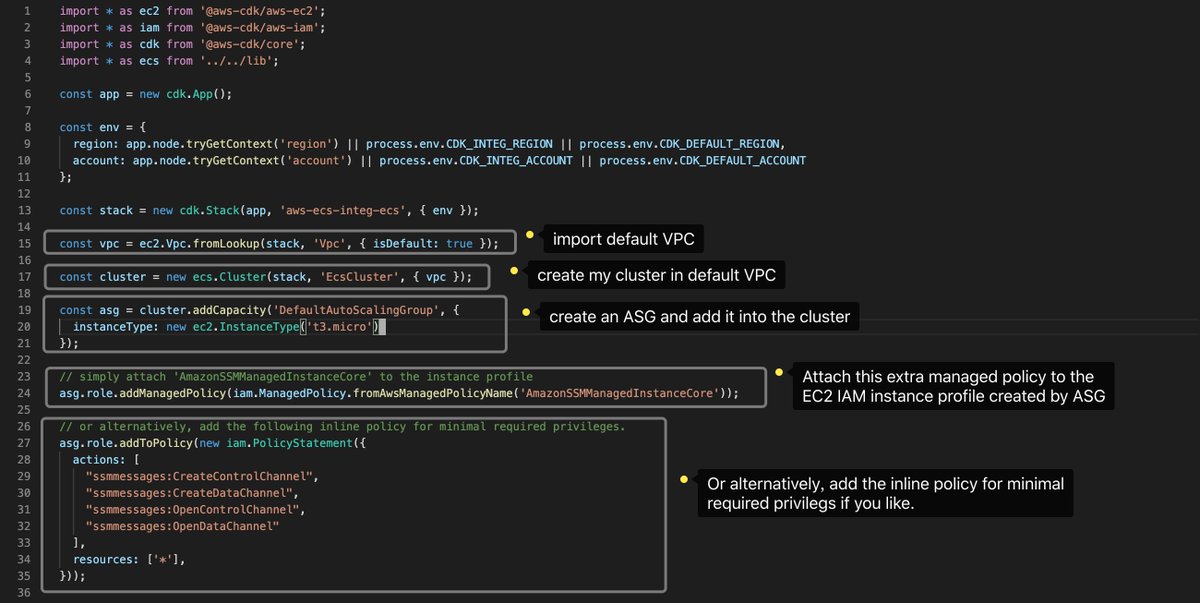



Pahudnet The Interesting Thing Is That I Can Just Write 2 Or 3 Awscdk Statements Like This To Bring Up My Amazon Ecs Cluster With Latest Amazon Ecs Optimized Linux 2



Cool Assessment Terraform Pentestportal Iam Tf At Develop Cisagov Cool Assessment Terraform Github



1
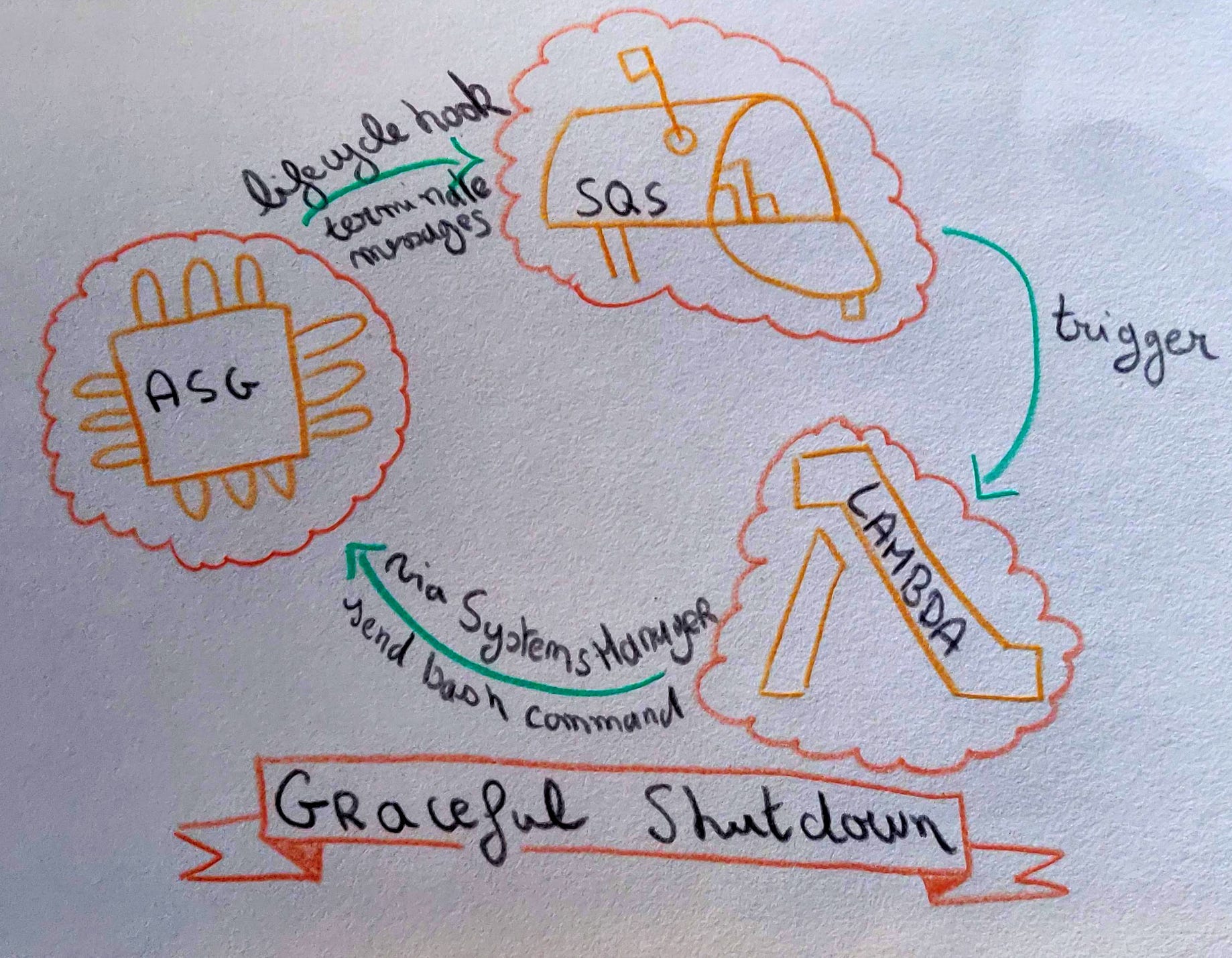



Graceful Shutdown Using Simple Sytems Manager And Terraform On Aws By Paul Leclercq Hawk Labs Medium




Iac Mit Aws Cdk



Github Rhythmictech Terraform Aws Atlassian Bitbucket Creates A Bitbucket Ec2 Instance And Elb
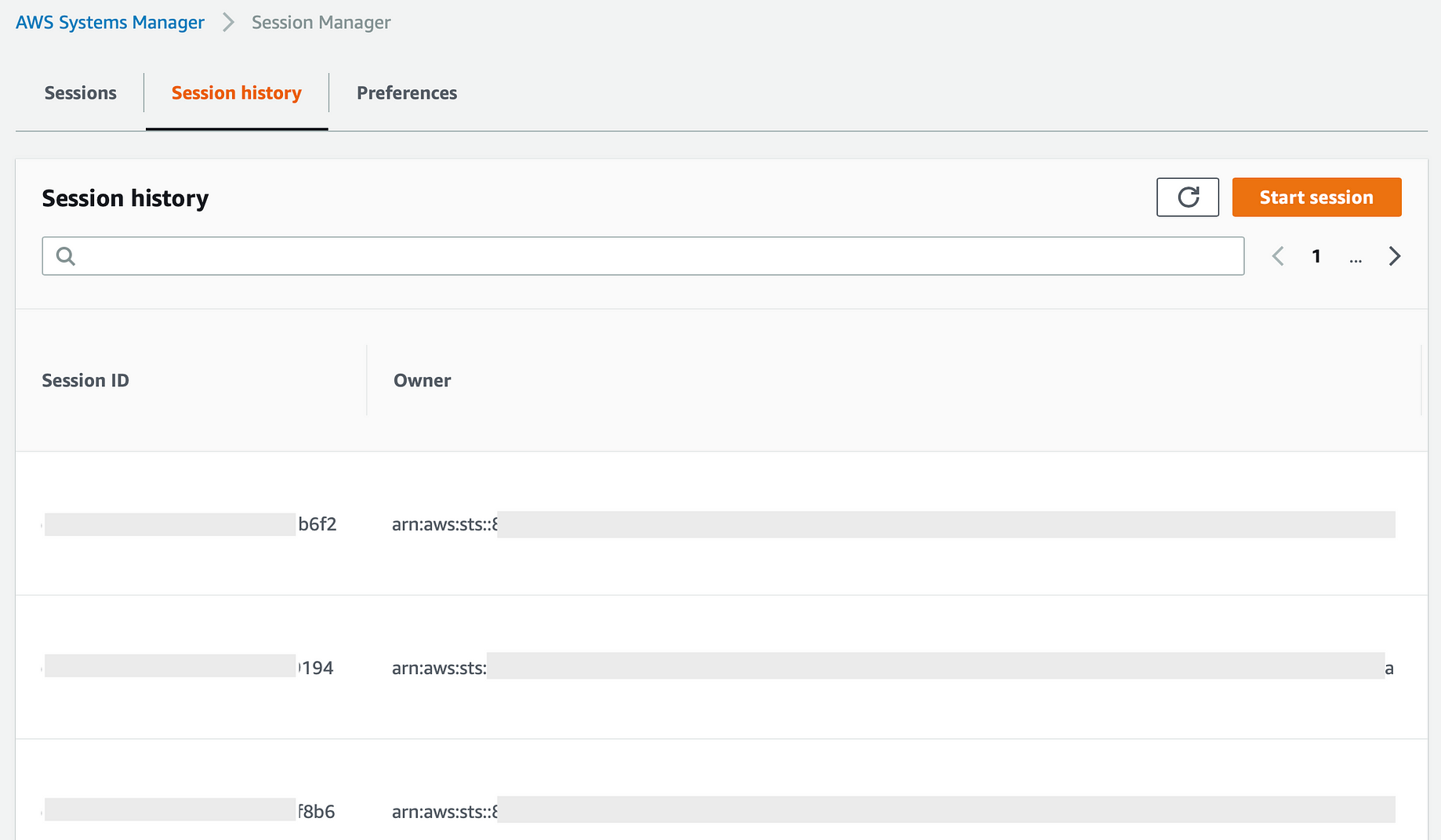



Going Bastion Less Accessing Private Ec2 Instance With Session Manager By Daniel Da Costa Towards Data Science
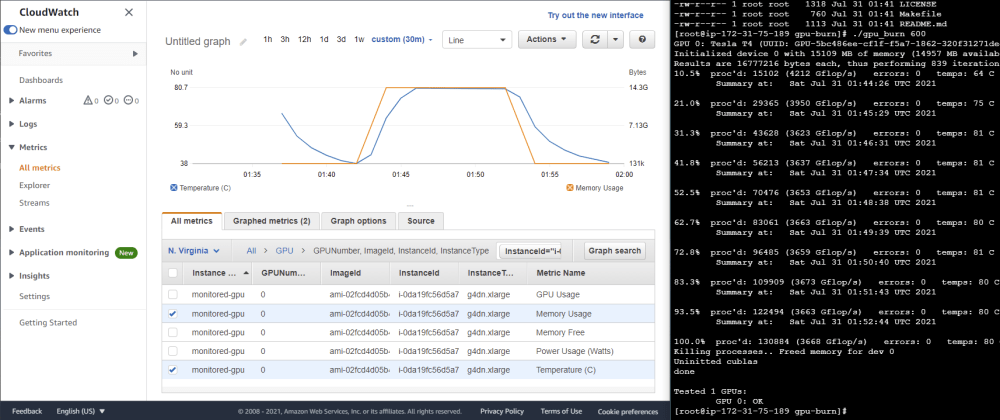



Instrumenting Amis For Gpu Monitoring On Cloudwatch Dev Community



Fv0wqjdk3ykemm



Rackspace Infrastructure Automation Aws Terraform Ec2 Asg Githubmemory
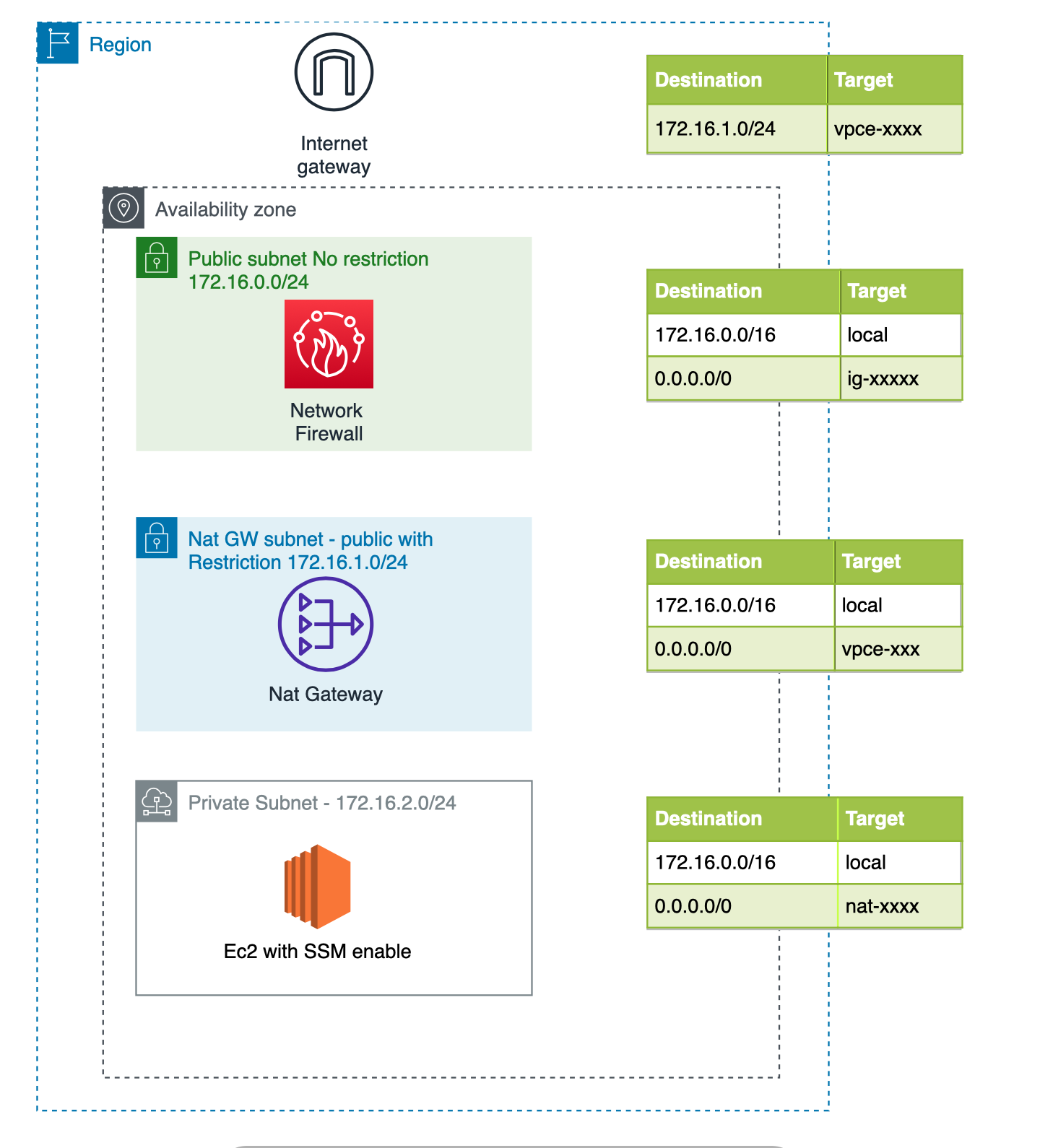



How To Build An Aws Network Firewall Environment By Giuseppe Borgese Medium



1
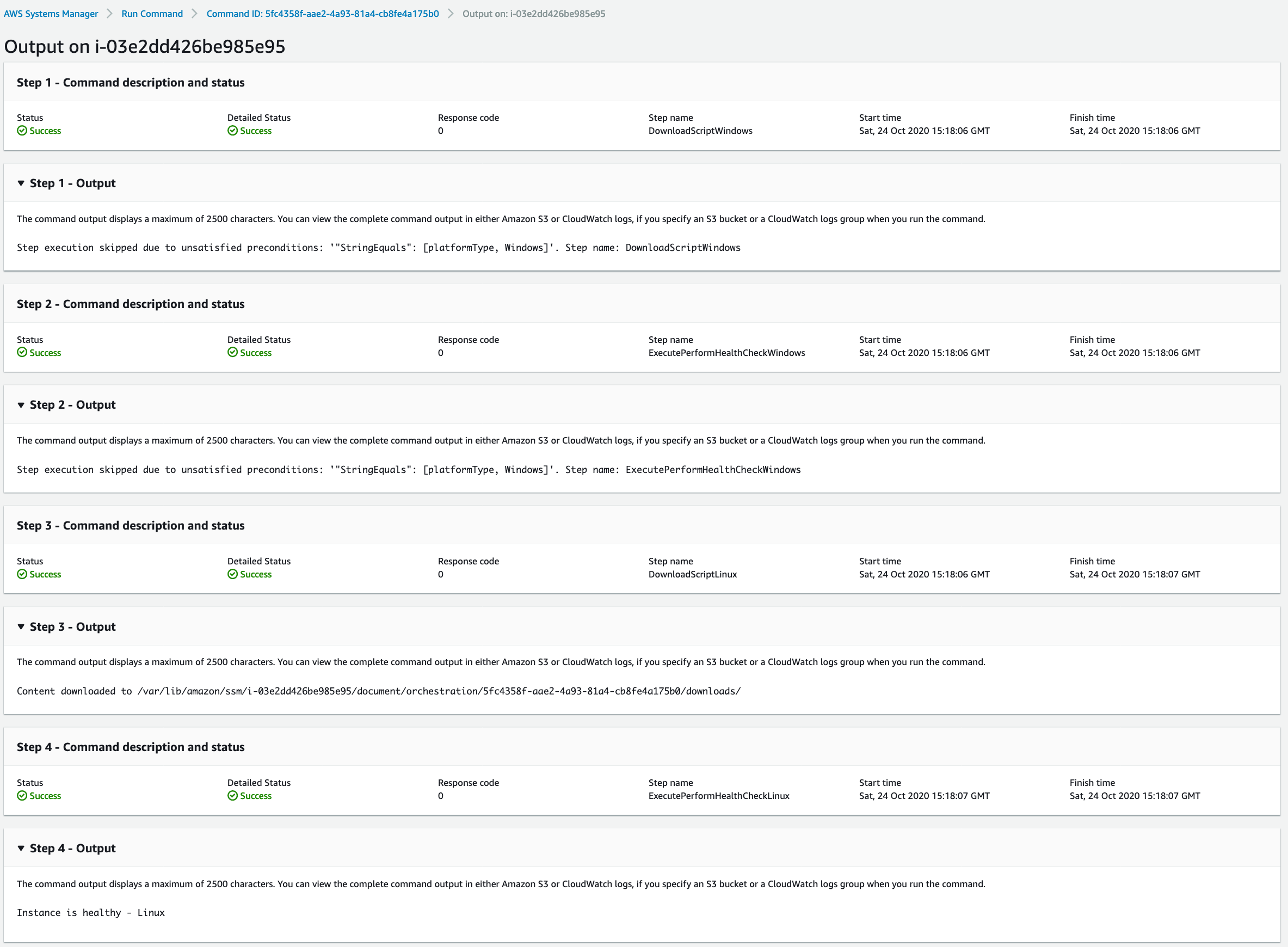



Automate Instance Hygiene With Aws Ssm Command Documents Jdheyburn




Substitute Your Ssh Bastions Using Aws Systems Manager



Aws Iam Role Policy Attachment Using Count And List Of Polices Returns An Inconsistent Result Error If The List Order Is Changed Issue Hashicorp Terraform Provider Aws Github




Securing Access To Emr Clusters Using Aws Systems Manager Aws Feed



Terraform Aws Ec2 And Ssm Aws System Manager By Khimananda Oli Medium



Terraform Provider Aws Githubmemory



Not Possible To Upgrade To Terraform 0 12 If Using Resource Aws Lb Listener Certificate Issue 8751 Hashicorp Terraform Provider Aws Github



Github Bridgecrewio Terraform Aws Session Manager Terraform Module For Deploying Aws Session Manager




Ohne Bastion Zugriff Auf Die Private Ec2 Instanz Mit Dem Sitzungsmanager




Bootstrapping A Startup On Aws With Aws Serverless And Go Devsday Ru
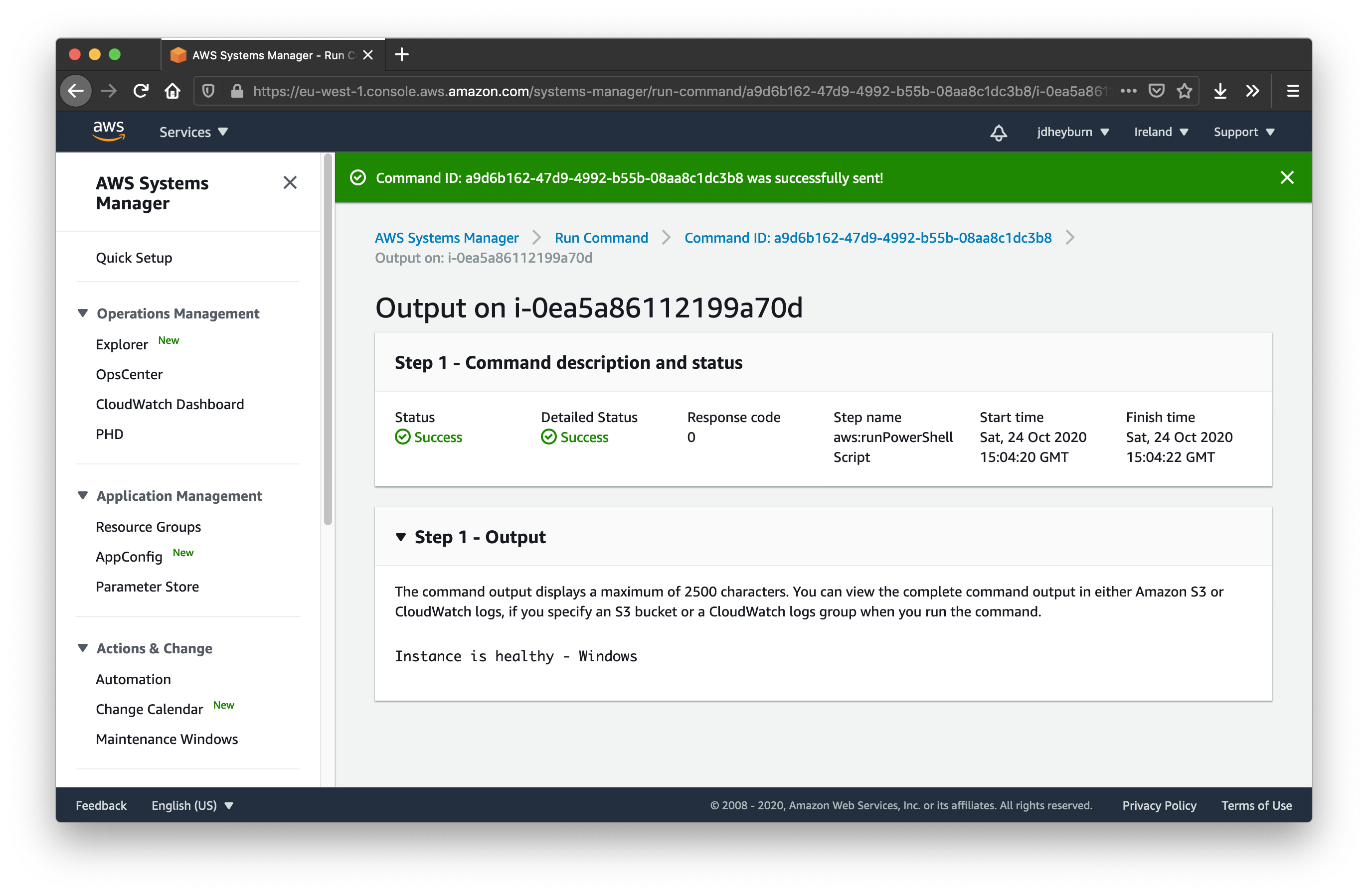



Automate Instance Hygiene With Aws Ssm Command Documents Jdheyburn



Terraform Aws Ec2 With Ssm Agent Installed




Terraform Multi Cloud Demo Part 3 Aws Infrastructure Dave S Blog




Terraform Multi Cloud Demo Part 3 Aws Infrastructure Dave S Blog




Terraform Aws Elastic Beanstalk Environment



Infosanity Blog Offensive And Defensive It Security




Terraform Cloud Stuck After Aws Session Timeout




Aws Session Manager Less Infrastructure More Features Sym Blog




Terraform Aws Eks Githubmemory




Using Aws Systems Manager Session Manager Kernel Talks



1



Going Bastion Less Accessing Private Ec2 Instance With Session Manager By Daniel Da Costa Towards Data Science



Can We Attach Iam Policies To The Iam Role Created For The Managed Node Group Issue 1258 Terraform Aws Modules Terraform Aws Eks Github




Automate Instance Hygiene With Aws Ssm Command Documents Jdheyburn



Github Notarize Terraform Aws Ec2 Asg



2




Gruntwork Newsletter November By Amanda Ohmer Gruntwork




Microsoft Sccm Admins Get Started With Aws Systems Manager Patch Manager Aws Management Governance Blog




Terraformでec2を使ったweb環境をつくろう Qiita



Intelematics Aws Ssm Ssh Proxycommand Giters




Hyvd1kwdhj6vbm



How To Connect An Ec2 Instance Via Systems Manager By Mert Saygi Medium
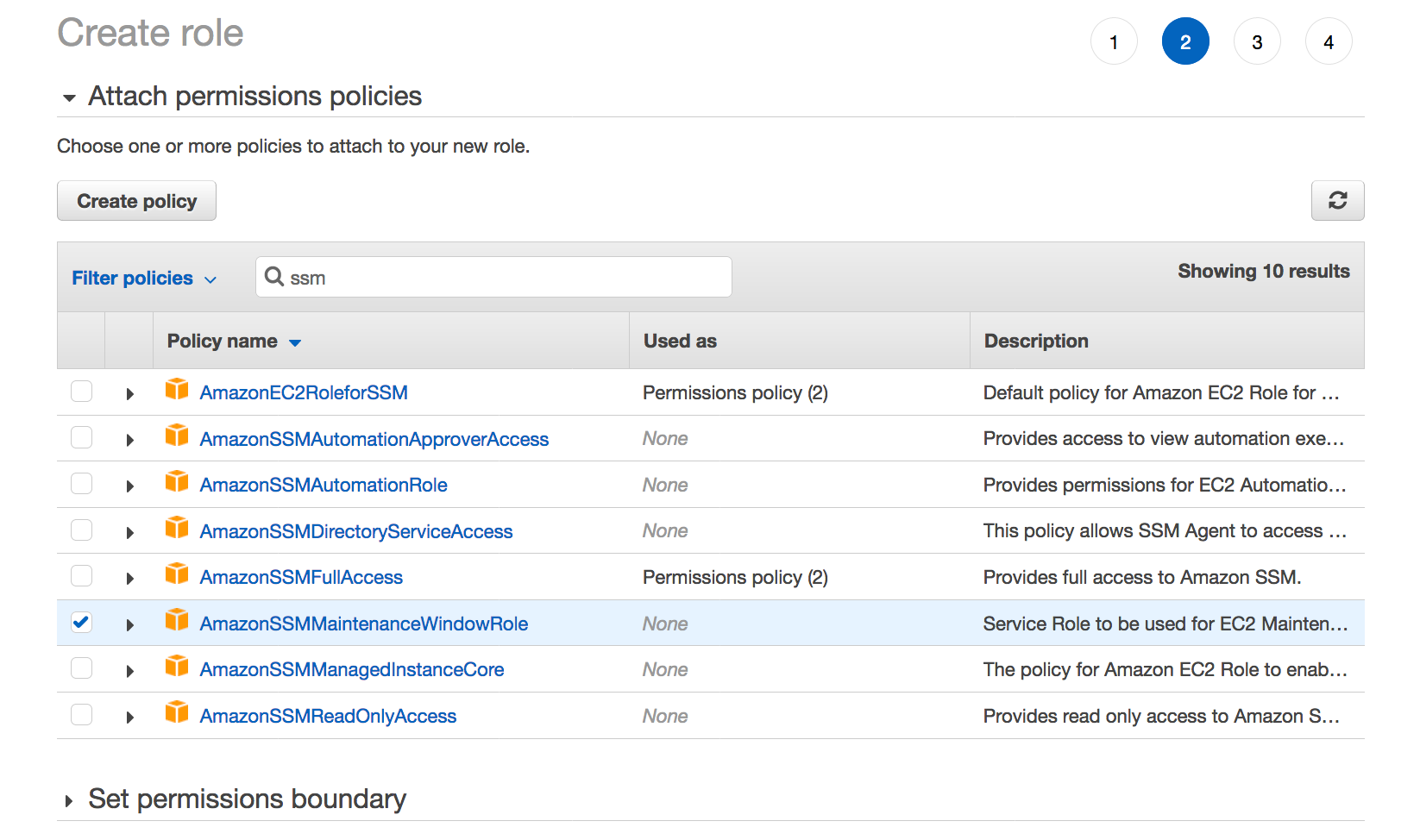



100 Days Of Devops Day 37 Automate The Process Of Ami Creation Using System Manager Maintenance Windows By Prashant Lakhera Medium



Boilerplate For A Basic Aws Infrastructure With Eks Cluster




Setting Up A Bottlerocket Managed Node Group On Amazon Eks With Terraform Containers




Ssh Logging And Session Management Using Aws Ssm Toptal
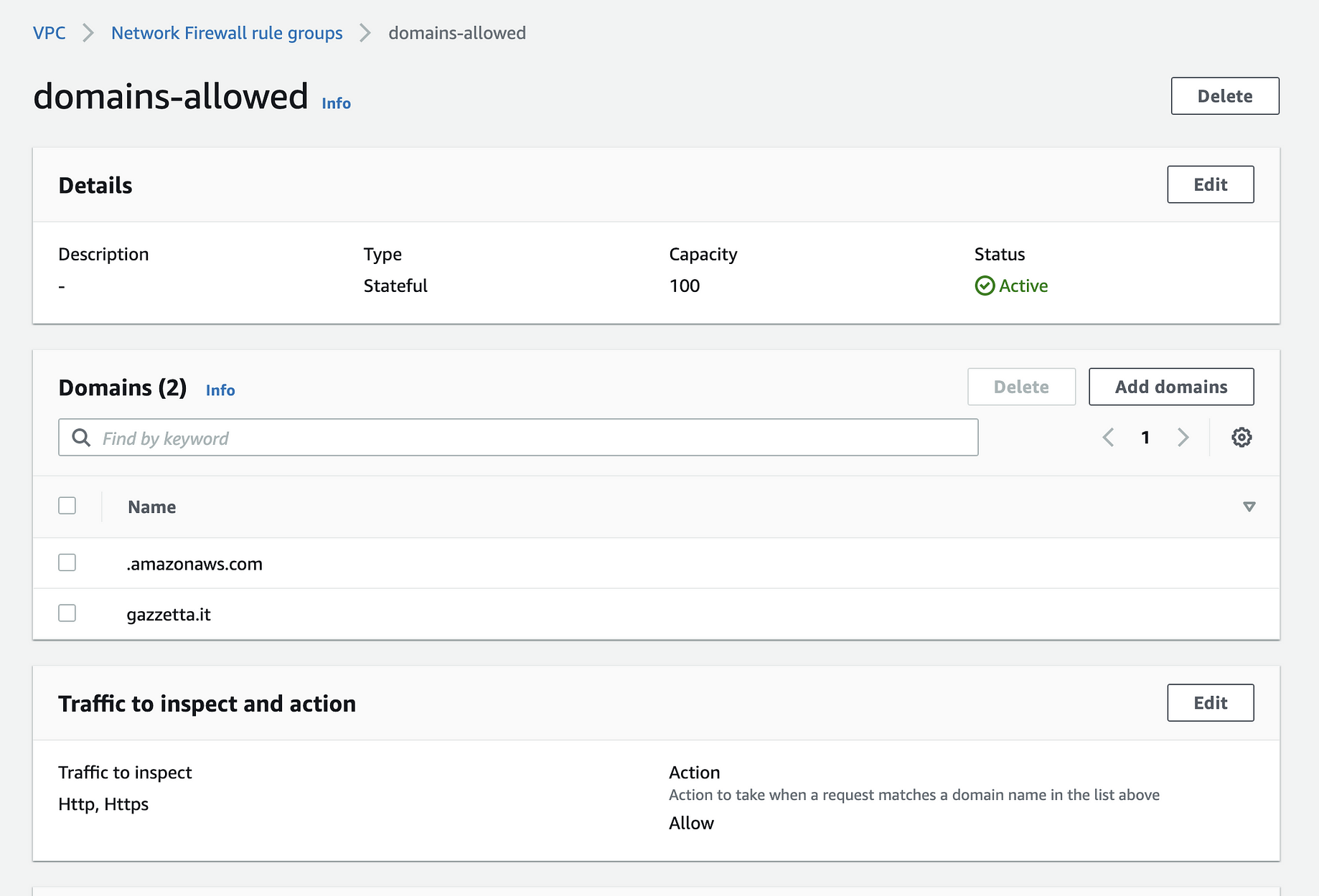



How To Build An Aws Network Firewall Environment By Giuseppe Borgese Medium




Setting Up A Bottlerocket Managed Node Group On Amazon Eks With Terraform Containers
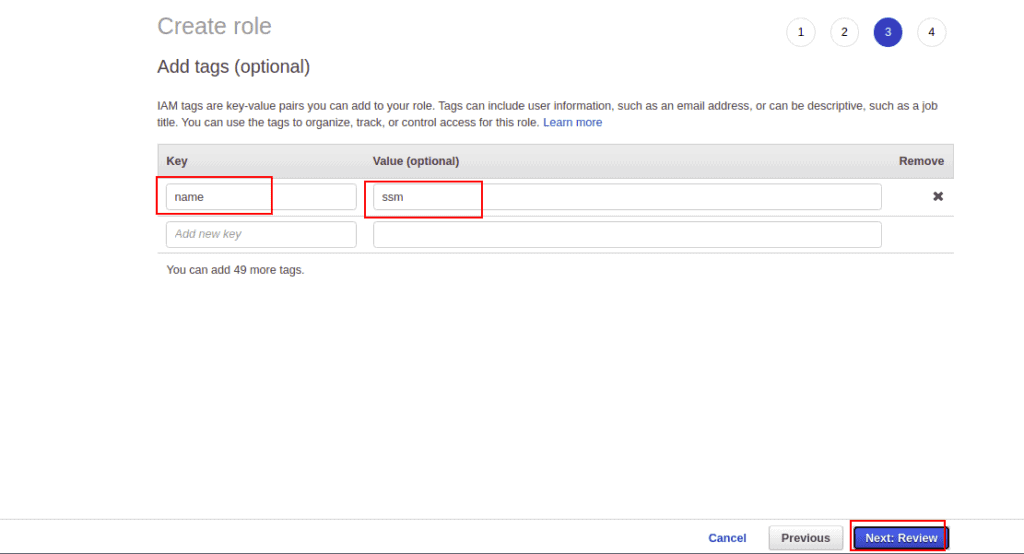



Introduction To Aws Systems Manager




Secure Rds Access Through Ssh Tunneling Over Aws Ssm In Terraform




Chaos Engineering Mit Dem Aws Fault Injection Service Fis




Improve Monitoring Of Aws Systems Manager Agent Aws Management Governance Blog



Github Bridgecrewio Terraform Aws Session Manager Terraform Module For Deploying Aws Session Manager
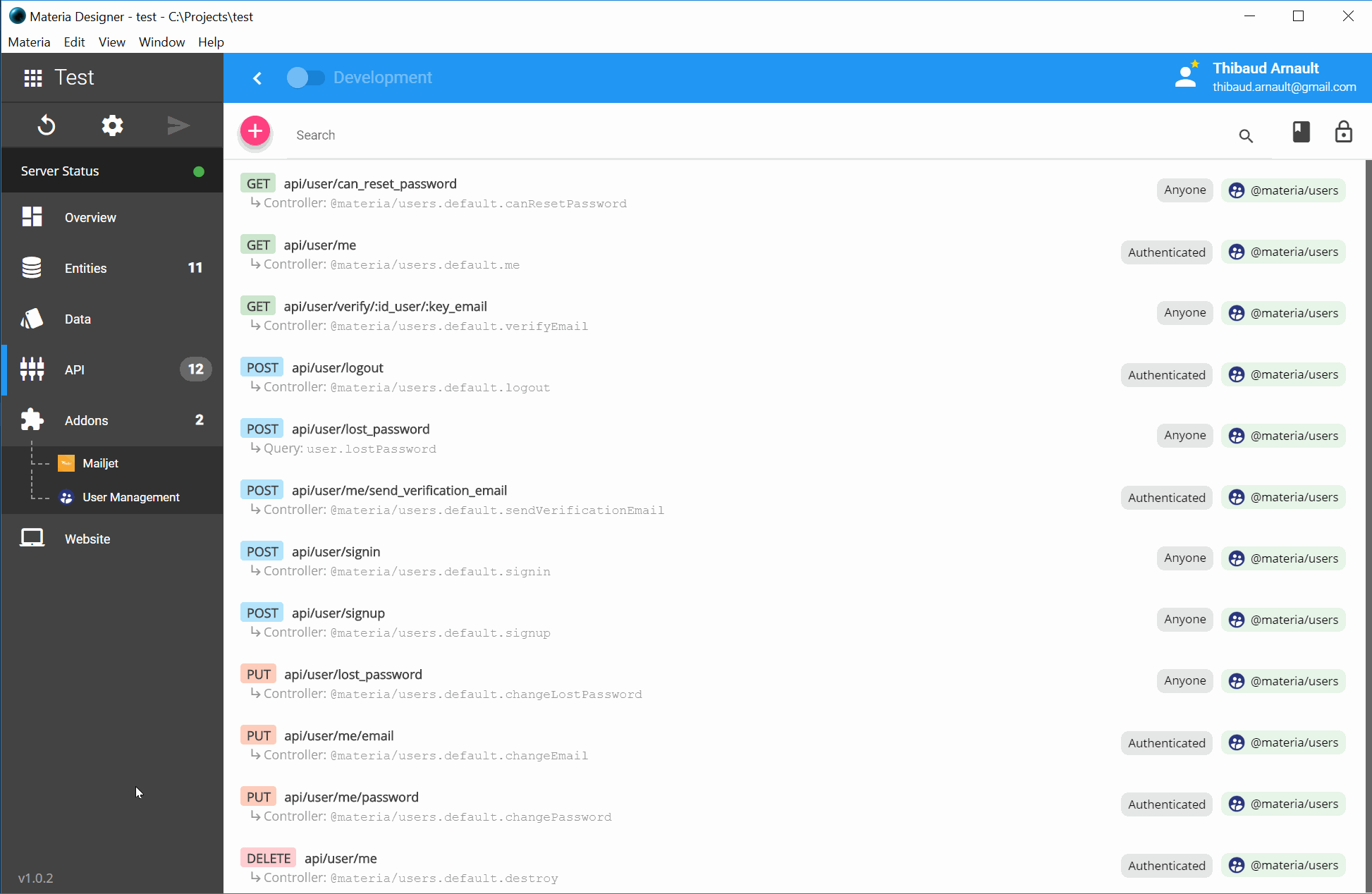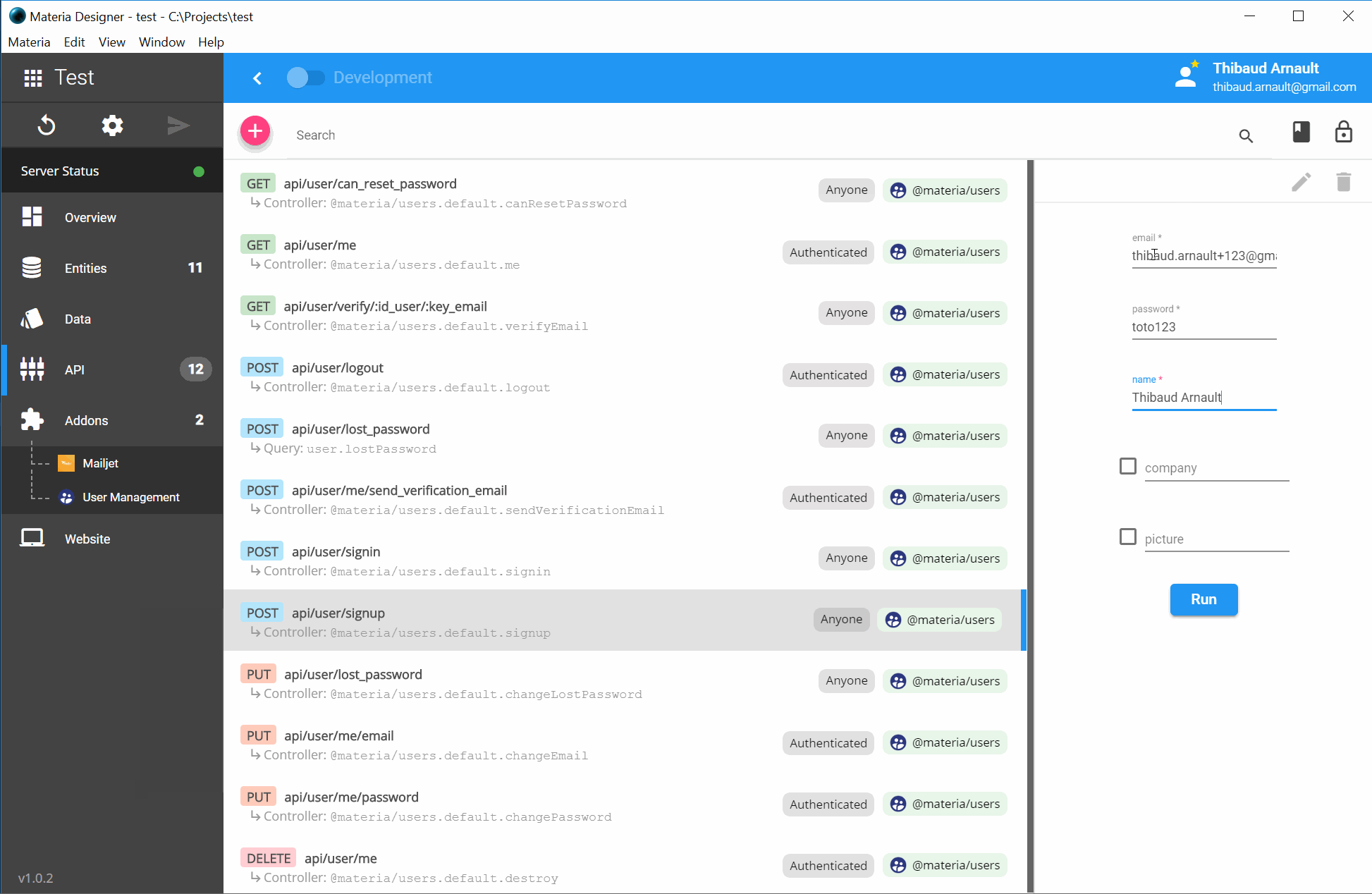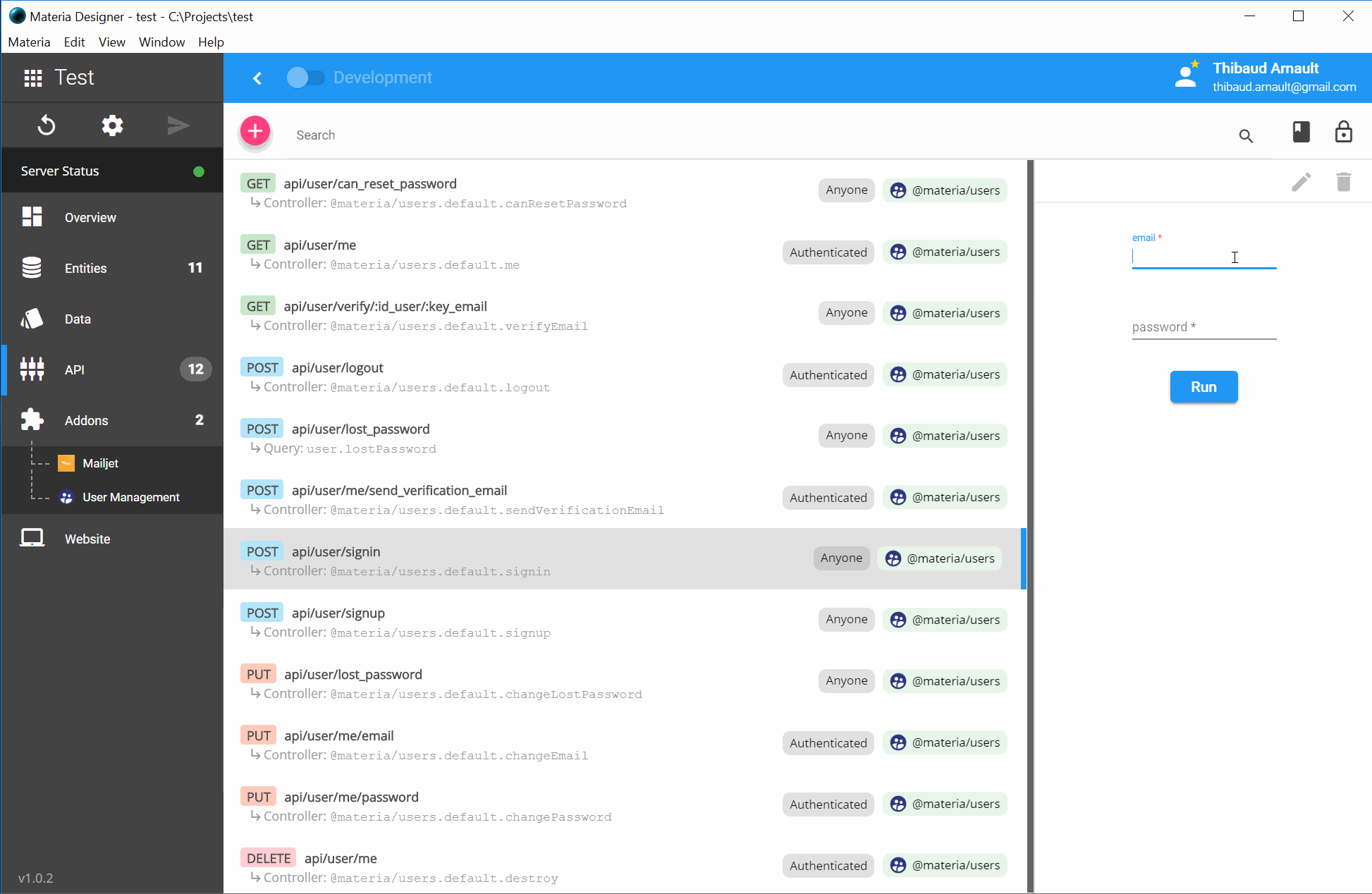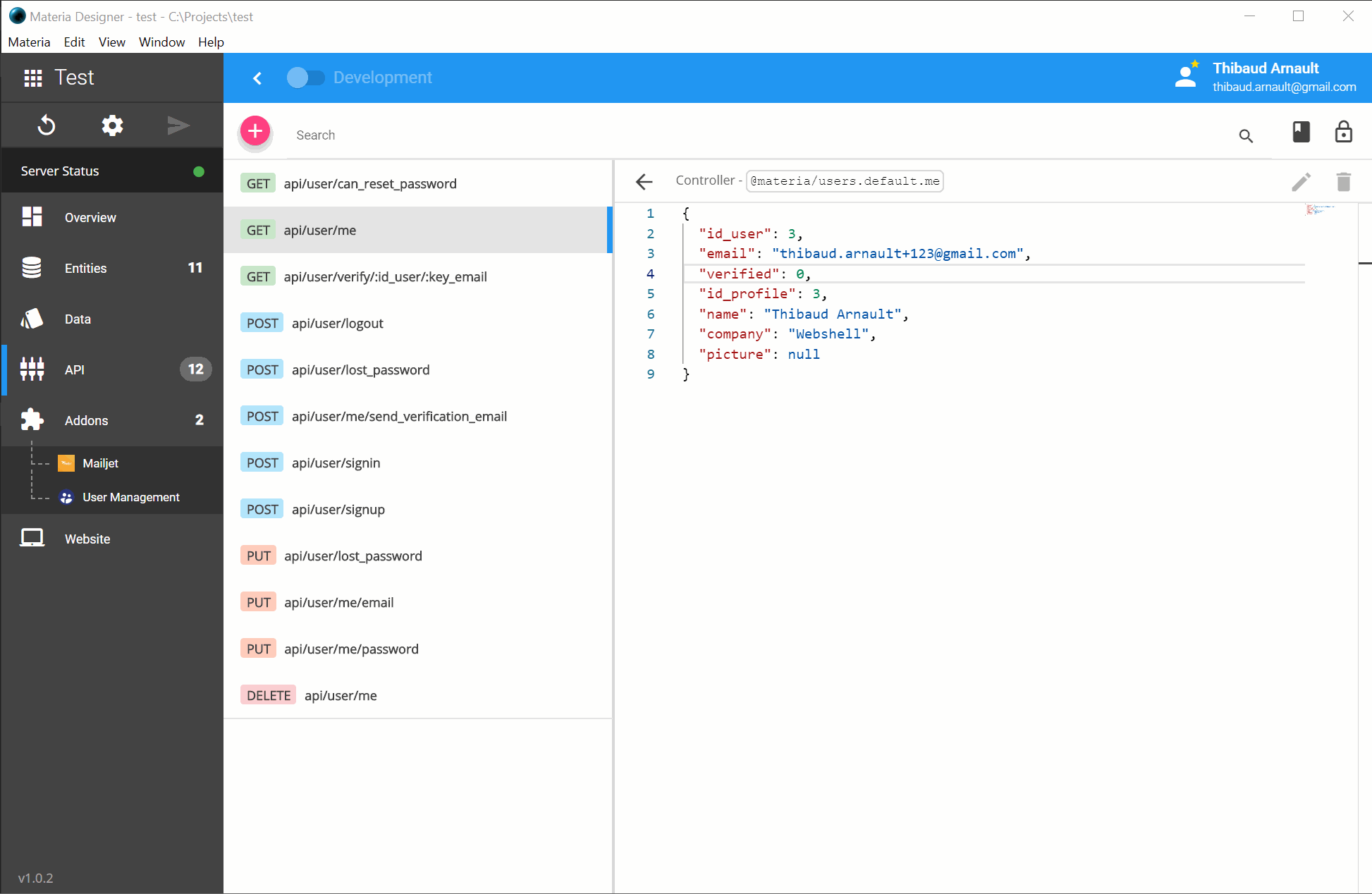



Terraform Aws Ec2 And Ssm Aws System Manager By Khimananda Oli Medium



Add Ssm Session Manager Support Issue 121 Npalm Terraform Aws Gitlab Runner Github
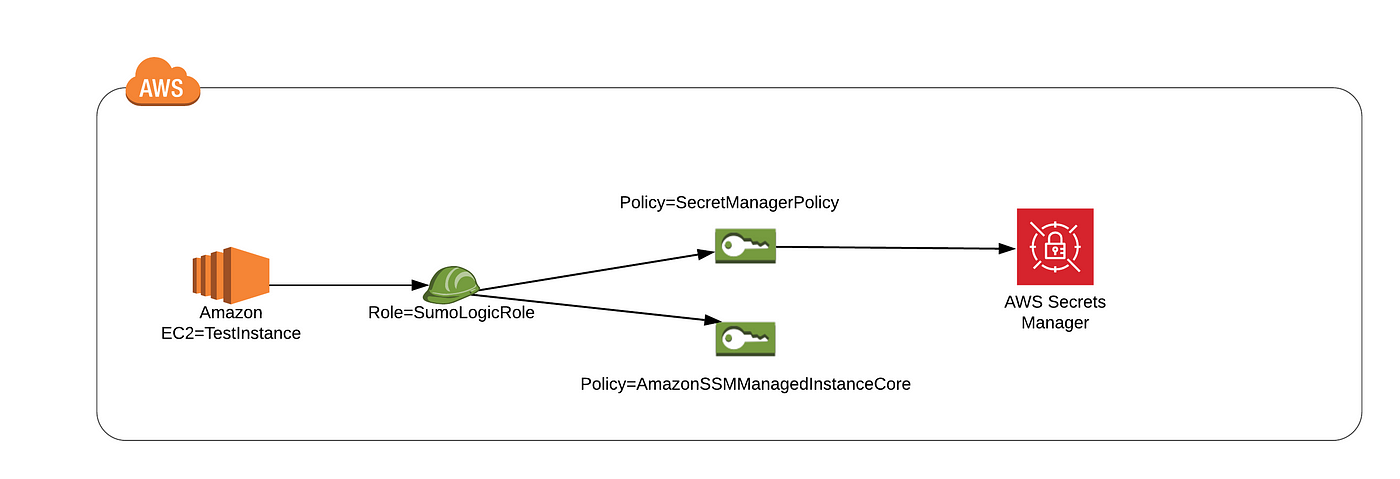



Dewashish Pramanik Medium
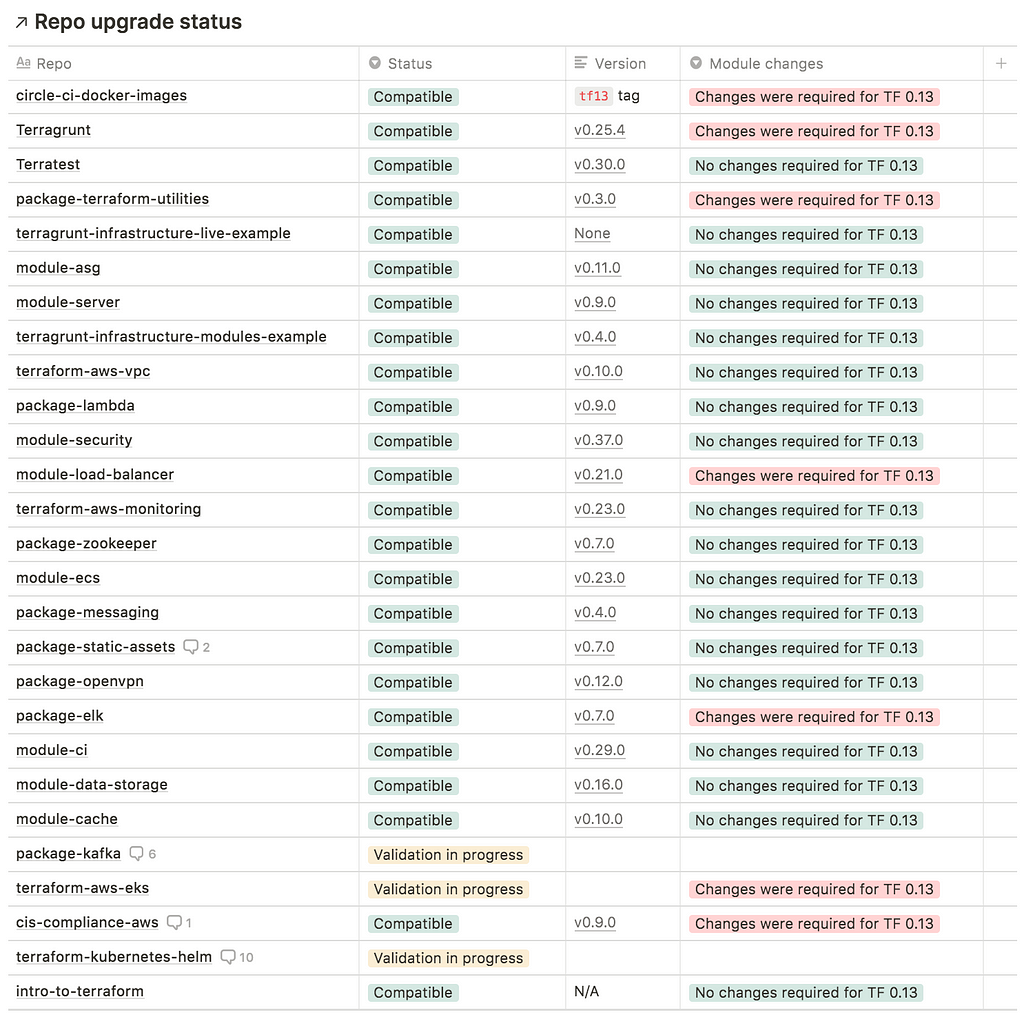



Gruntwork Newsletter November Laptrinhx
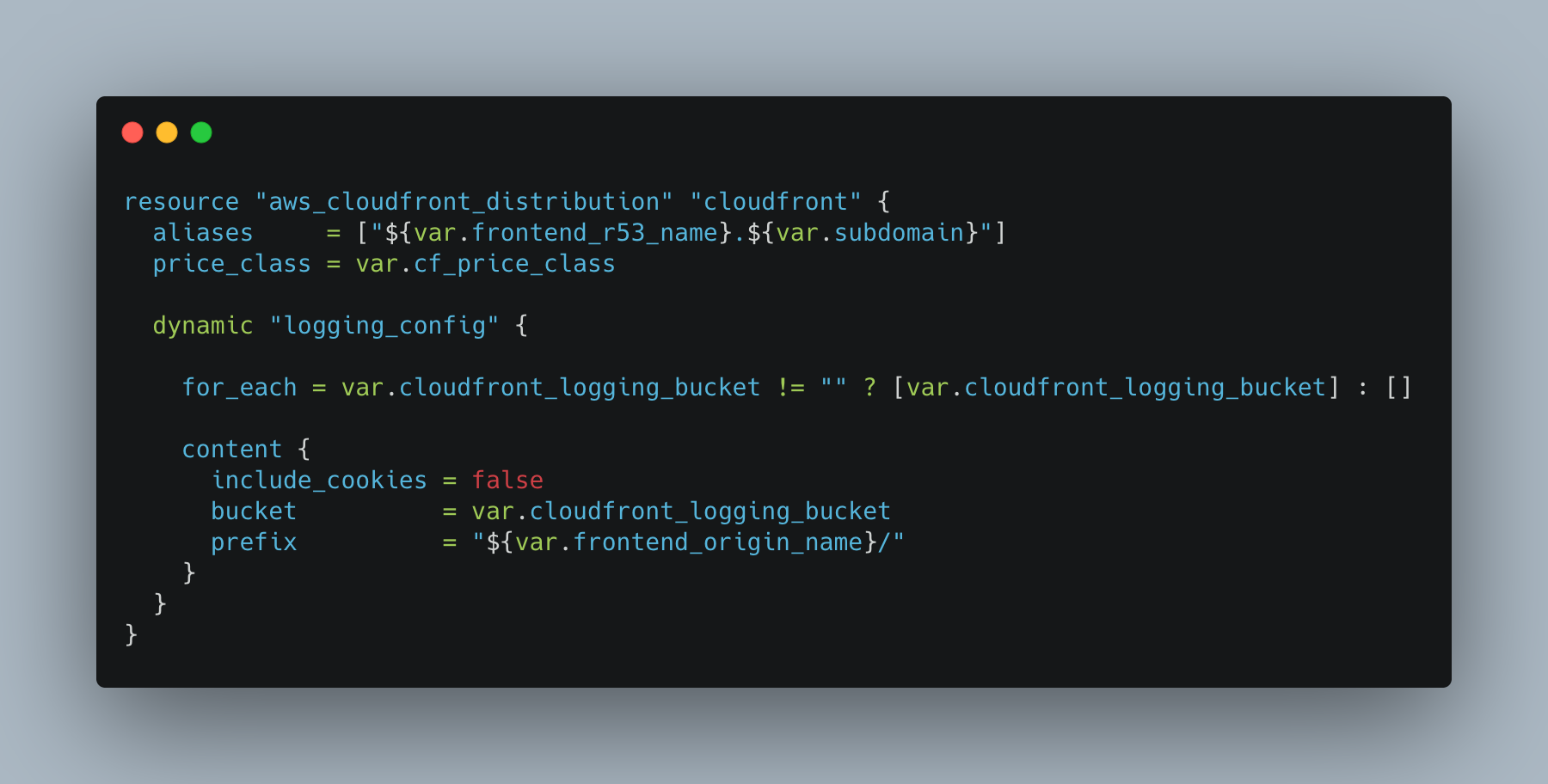



Ditch Ssh For Good With Aws Ssm Session Manager By G Sre Aug 21 Medium




Bugcjn4cxbwfzm
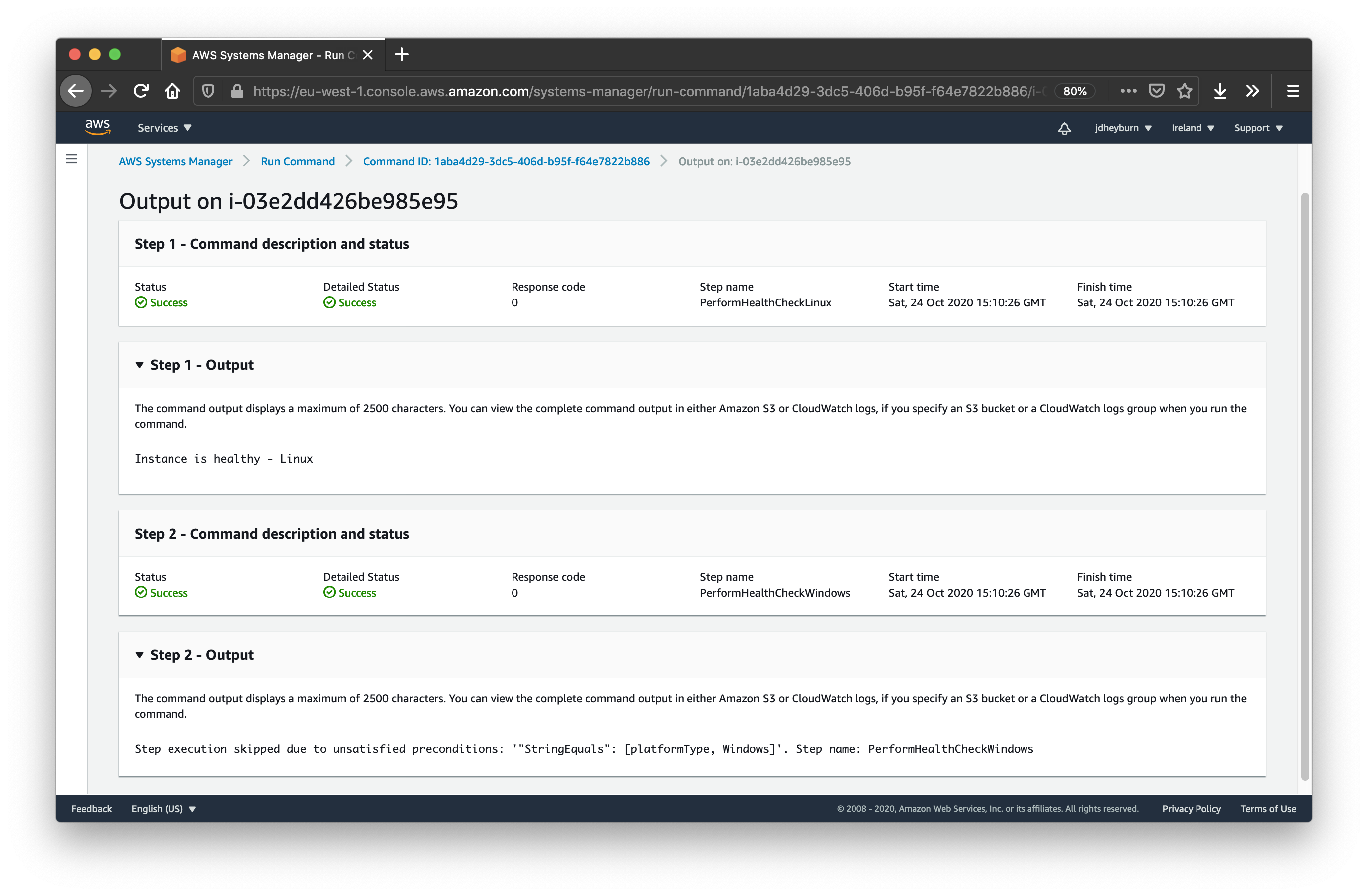



Automate Instance Hygiene With Aws Ssm Command Documents Jdheyburn




Improve Monitoring Of Aws Systems Manager Agent Aws Management Governance Blog
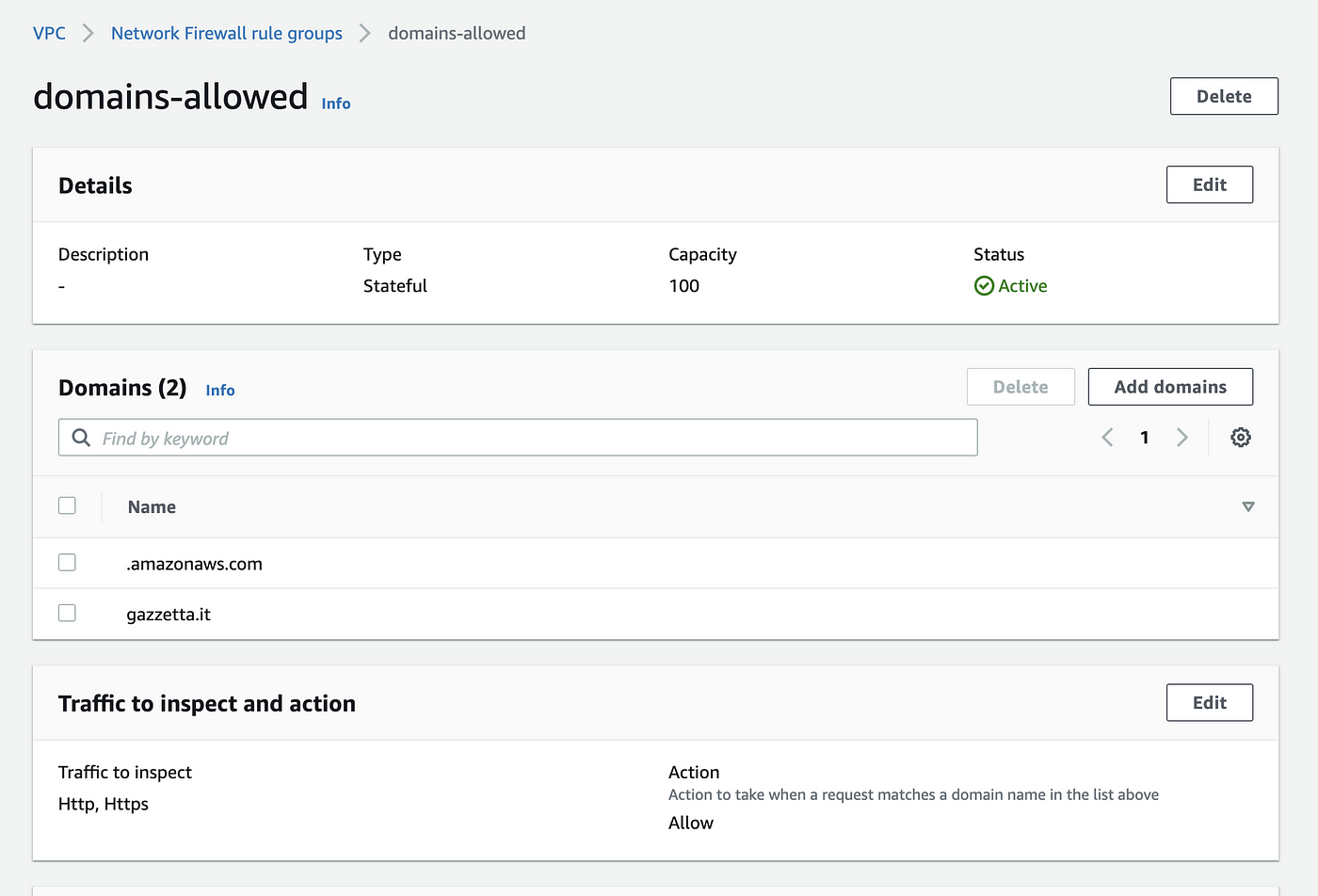



How To Build An Aws Network Firewall Environment By Giuseppe Borgese Medium



Terraform Aws Ec2 And Ssm Aws System Manager By Khimananda Oli Medium



Aws Iam Policy Attachment Error When Attaching Amazon Managed Policies Issue 5979 Hashicorp Terraform Github


